
Orlando WordPress Developers
This week at M5 Design Studio, we have received phone calls from Orlando business owners whose websites were hacked. This is because of a vulnerability to a WordPress plugin called File Manager, which caused millions of websites to be hacked over the past weekend. While none of our websites were attacked, we want to provide this resource to ensure you are protecting yourself from attack due to this vulnerability.
The File Manager plugin is used to manage your website’s files directly from the admin dashboard of the website, rather than having to manage files externally. Wordfence estimates that of the 700,000 websites currently using File Manager, around 37% are still running vulnerable versions of the plugin.
Wordfence recorded 1.4 million attacks on WordPress websites by bots last week, including websites that are not currently running File Manager. The bots probe any WordPress website to identify and exploit old versions of the plugin. Keep in mind, this number only represents the WordPress websites currently protected by Wordfence. When considering all WordPress websites, the actual number of attacks will be much higher.
We found that two of the viruses that hackers installed are “donatelloflowfirstly.ga” and “lowerbeforwarden.ml.” In this article, we outline basic information about these viruses and how to remove it from your website. We also provide general steps to protect yourself from attacks on the File Manager vulnerability.
Removing the Viruses “lowerbeforwarden.ml” & “donatelloflowfirstly.ga”
The “lowerbeforwarden.ml” & “donatelloflowfirstly.ga” viruses redirect you to another page when you try to log into the WordPress admin dashboard for your site. The page we were redirected to contains this image:
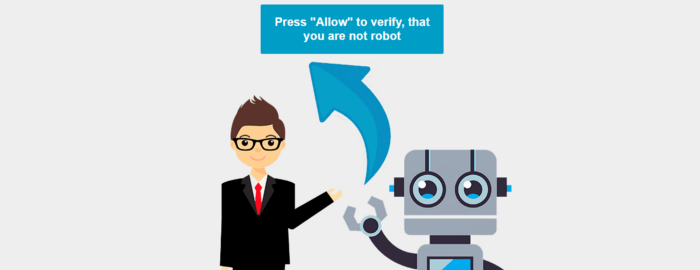
The virus installs a script throughout the website. If your website is infected, these are two examples of scripts that may be installed:
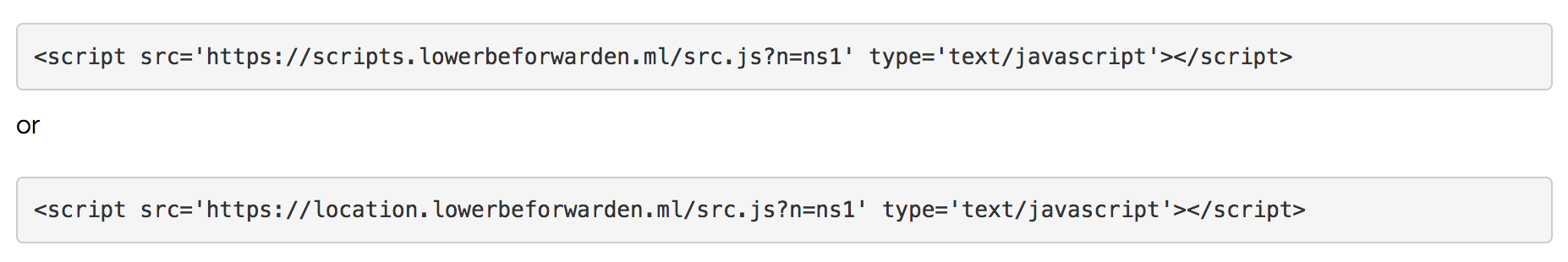
Most hosting companies offer malware and scan detection, but some of these services do not include scanning the database. In that case, the malware detection will not be sufficient to remove the virus. In order to remove the virus, we recommend the following.
-
Uninstall & Delete File Manager
You should uninstall and delete File Manager immediately. This is not an essential plugin for your website and can be deleted.
2. Remove the Script from Your Website
Option 1: Scan the Website with a Plugin
Scan your website and find the virus using an antivirus & malware software or plugin, such as Wordfence or Sucuri. This can be done by your web hosting, or you can do it with a WordPress plugin.
Option 2: Scan the Website Manually & Replace Core Files
If that doesn’t solve the issue, then we recommend this:
Manually search for the script in the database and scan all files in the server. This article gives step-by-step instructions to help you find and remove the virus.
You will need to then remove the core files from the website and replace them with a new, uncorrupted copy.
3. Remove Script from Your Computer
We found that after scanning the files and cleaning the script from the website, we still couldn’t enter the website. We had to also clean the script from the computer using an antivirus and malware software before we could enter the website.
Prevent Attacks on File Manager Vulnerability
If you are using the File Manager plugin, here are steps to take to protect your website from bots that are seeking to exploit File Manager vulnerabilities.
-
Update File Manager to Version 6.9
If you are currently using the plugin, make sure it is updated to the most recent version, which has been corrected for security against this vulnerability.
-
Uninstall the Plugin if Unneeded
If you are not currently using the File Manager plugin, uninstall it from your website. You can reinstall it if or when you need it in the future. In the meantime, it is better to limit your site’s vulnerability by uninstalling a plugin that gives such wide access to file management.
-
Regular Scans
Schedule and conduct regular security scans on your website with a security and malware plugin such as Wordfence or Sucuri.
Orlando WordPress Maintenance
If you would like to have the support of Orlando WordPress experts to respond to attacks on this plugin’s vulnerability, contact us online or call us at (407) 968-6296. Our team of expert WordPress developers & designers is happy to help. M5 Design Studio is a web design, graphic design, and digital marketing agency located in Orlando, Florida.






